“`SIEM (Security Information and Event Management) tools are essential for organizations to detect and respond to security threats in real-time. With the increasing number of cyber attacks and data breaches, it is crucial to have a SIEM tool in place to monitor and analyze security events across the network. SIEM tools collect and correlate data from various sources, such as firewalls, intrusion detection systems, and antivirus software, to provide a comprehensive view of the security posture of the organization. This helps security teams to identify potential threats and respond to them quickly before they cause any damage.
Additionally, SIEM tools provide compliance reporting, which is necessary for organizations to meet regulatory requirements. Overall, SIEM tools are necessary to ensure the security and integrity of an organization’s
What is the benefit of a SIEM?
A well-designed SIEM platform can offer numerous security benefits to an organization by automating threat detection. These advantages include the ability to detect and control malware from endpoint to perimeter, as well as providing boundary defenses through firewalls, routers, VPNs, and other network resources. By utilizing a SIEM platform, organizations can improve their overall security posture and reduce the risk of cyber attacks.
What are the three main roles of a SIEM?
A Security Information and Event Management (SIEM) system has three main roles: log management, security information management, and security event management. Log management involves collecting and storing logs from various sources, such as servers, applications, and network devices. Security information management involves analyzing and correlating the logs to identify security threats and vulnerabilities. Security event management involves responding to security incidents by alerting security personnel and initiating incident response procedures.
A SIEM system provides real-time monitoring and analysis of security events, enabling organizations to detect and respond to security threats quickly and effectively.
What is the main advantage of a SIEM compared to a normal log collector?
SIEM, or Security Information and Event Management, is a powerful tool for enhancing security measures. Like log management, the primary objective of SIEM is to ensure security, and its effectiveness is directly proportional to the quality of data it can access. However, the benefits of SIEM go beyond just data access. One of the most significant advantages of SIEM is its ability to analyze data in real-time, providing immediate insights into potential security threats.
Additionally, SIEM can connect different systems, unifying information in a single console, making it easier to manage and monitor security events. These features make SIEM an essential tool for any organization looking to enhance its security posture.
What problem does SIEM solve?
SIEM, or Security Information and Event Management, is a powerful tool that can help organizations bring together internal data to generate alerts. These alerts are crucial for detecting any suspicious activities within a company. However, without proper context and content, people may not fully understand the significance of these alerts. It is important to ensure that the alerts generated by SIEM are accompanied by clear and concise information, so that individuals can take appropriate action to address any potential security threats.
What are the benefits of SIEM and SOC?
SIEMs, or Security Information and Event Management tools, have become a crucial component of Security Operations Centers (SOCs). As businesses become more reliant on IT networks, it becomes increasingly challenging to manually monitor entire systems and analyze vast amounts of data. SIEM tools automate the process of threat detection, allowing SOCs to save resources and labor while improving efficiency and productivity. With the ability to detect and respond to security incidents in real-time, SIEMs are an indispensable tool for any organization looking to enhance their security posture.
Can SIEM prevent attacks?
SIEM, or Security Information and Event Management, is a cybersecurity approach that can effectively prevent ransomware attacks. This comprehensive strategy involves a range of cybersecurity solutions, including threat detection tools, analytics software, and response mechanisms. By utilizing SIEM, organizations can proactively identify and mitigate potential threats before they can cause significant damage. With its multifaceted approach, SIEM is a powerful tool for safeguarding against ransomware attacks and other cybersecurity threats.
What can SIEM detect?
SIEMs, or Security Information and Event Management systems, are capable of detecting lateral movement by analyzing data from various IT systems. In addition, they can also monitor data from mobile devices used by employees and identify any unusual activity that may indicate a potential data breach. This is particularly important in today’s mobile workforce, where employees often use their personal devices to access company data. By using a SIEM, organizations can ensure that their sensitive information remains secure and protected from unauthorized access.
Numerous studies have shown that implementing a SIEM can significantly reduce the risk of data breaches and improve overall cybersecurity posture.
Is SIEM a vulnerability scanner?
SIEM, which stands for Security Information and Event Management, is a powerful tool that can help organizations monitor their IT environment and stay ahead of potential security threats. By providing real-time intelligence and actionable insights, SIEM solutions enable security teams to proactively manage vulnerabilities and prevent attacks before they occur. With the increasing sophistication of cyber threats, investing in a SIEM solution is becoming more important than ever for businesses of all sizes. Whether you’re a small startup or a large enterprise, implementing a SIEM solution can help you stay one step ahead of the bad guys and keep your sensitive data safe and secure.
How does SIEM detect threats?
SIEM systems are a powerful tool for organizations to monitor their security posture and detect potential threats. By collecting and analyzing log data from various sources, these systems provide a comprehensive view of an organization’s security landscape. With advanced analytics, SIEM systems can identify and respond to potential security threats before they become serious. This proactive approach to security can help organizations stay ahead of the curve and protect their sensitive data and assets.
Who should use SIEM?
SIEM, or Security Information and Event Management, is a versatile tool that companies can use for a multitude of purposes related to data and logs. It can be used for security programs, audit and compliance reporting, help desk support, and network troubleshooting. One of the key benefits of SIEM is its ability to handle large amounts of data, which means that organizations can easily expand and add more data as needed. This makes SIEM a valuable asset for companies of all sizes, especially those that deal with sensitive information or have complex IT infrastructures.
How does SIEM collect data?
The collection of data by SIEM can be done in four different ways. The most common method is by installing an agent on the device. Another way is by directly connecting to the device using a network protocol or API call. Additionally, data can be collected by accessing log files directly from storage, which are usually in Syslog format.
These methods provide flexibility in data collection and allow for a comprehensive view of the security landscape.
What are the components of SIEM?
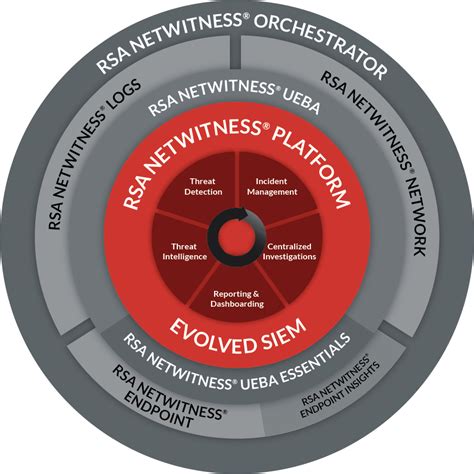
SIEM architecture is composed of several key components that work together to provide effective security monitoring. One of the most important components is log and data collection, which involves gathering information from various sources such as network devices, servers, and applications. Once the data is collected, it must be normalized to ensure that it can be easily analyzed and compared. Another critical component is log correlation, which involves identifying patterns and relationships between different events to detect potential security threats.
By leveraging these components, organizations can gain greater visibility into their security posture and respond more effectively to potential threats.
Is a SIEM a firewall?
SIEM and firewall are two distinct tools that serve different purposes in network security. A firewall is designed to prevent malicious content from infiltrating your network, while SIEM is a threat detection and data collection tool. SIEM collects and analyzes log data from various network security solutions, including the firewall. By doing so, it can identify potential threats and provide insights into network activity.
While a firewall is essential for preventing attacks, SIEM is crucial for detecting and responding to them. Together, these tools provide a comprehensive approach to network security.
What are two examples of SIEM?
What is a SIEM example?
If you’re familiar with cybersecurity, you may have heard of some popular SIEM (Security Information and Event Management) software options such as ArcSight ESM, AT&T Cybersecurity (previously known as AlienVault), Fortinet, IBM QRadar, McAfee SIEM, and Splunk. However, due to the software’s extensive capabilities and resource requirements, it may not be a feasible choice for smaller businesses.
What are the features of SIEM solution?
SIEM (Security Information and Event Management) solutions are designed to provide comprehensive security monitoring and threat detection capabilities for organizations. Some of the key features of SIEM solutions include real-time event correlation and analysis, log management, threat intelligence integration, and incident response automation. SIEM solutions can collect and analyze data from various sources, including network devices, servers, applications, and endpoints, to identify security incidents and anomalies. They can also generate alerts and reports to help security teams investigate and respond to threats quickly and effectively.
Additionally, SIEM solutions can help organizations comply with regulatory requirements by providing audit trails and evidence of security controls. Overall, SIEM solutions are essential tools for organizations that want to improve their security posture and protect against cyber threats.
What can a SIEM detect?
A Security Information and Event Management (SIEM) system can detect a wide range of security threats and anomalies in an organization’s network. It can monitor network traffic, log files, and system events to identify potential security breaches, such as unauthorized access attempts, malware infections, and data exfiltration. SIEM can also detect unusual user behavior, such as login attempts from unusual locations or at unusual times. Additionally, SIEM can correlate events from multiple sources to identify complex attacks that may go unnoticed by other security tools.
Overall, a SIEM is a powerful tool for detecting and responding to security incidents in real-time, helping organizations to protect their sensitive data and assets from cyber threats.
How does SIEM detect threats?
SIEM systems are a powerful tool for organizations to monitor their security posture and detect potential threats. By collecting and analyzing log data from various sources, these systems provide a comprehensive view of an organization’s security landscape. With advanced analytics, SIEM systems can identify and respond to potential security threats before they become serious. This proactive approach to security can help organizations stay ahead of the curve and protect their sensitive data and assets.
What should I look for in a SIEM solution?
When looking for a SIEM (Security Information and Event Management) solution, there are several key factors to consider. Firstly, it should be able to collect and analyze data from various sources, including network devices, servers, and applications. It should also have advanced threat detection capabilities, such as machine learning and behavioral analysis, to identify and respond to potential security incidents. Additionally, it should provide real-time alerts and reporting, as well as the ability to investigate and remediate incidents.
Other important features to look for include scalability, ease of use, and integration with other security tools. It’s also important to consider the vendor’s reputation and customer support. Ultimately, the right SIEM solution will depend on your organization’s specific needs and budget.
Related Article
- Why Do We Fight On Vacation?
- Why Do We Crucify Him Again?
- Why Do We Celebrate Wang Zhenyi?
- Why Do We Celebrate Lebron James?
- Why Do We Celebrate Frida Kahlo?
- Why Do Wasps Like Car Mirrors?
- Why Do Wasps Keep Coming Back?
- Why Do Vw Smell Like Crayons?
- Why Do Vuse Pods Taste Burnt?
- Why Do Volleyball Players Wear Spandex?